
The security researchers from McAfee have detected a banking trojan that infects home and enterprise computers using universal plug and play (UPnP) for opening ports. Pinkslipbot, also called QakBot, continues to use infected machines as its control
server even after it’s removed. It’s, probably, the first malware that uses HTTPS-based control servers. McAfee has also released a free tool to take care of the infection.any people often question the intent of cyber criminals who aim to hurt the computer and internet users by infecting their computers with different kinds of malware. People should note that money is one of the biggest inspirations behind such activities. By using malware like banking trojans, spyware, adware and ransomware, notorious hackers earn tons of illegal money.
The security researchers at McAfee have uncovered a new form of banking malware, called Pinkslipbot, that has been using infected computers as its control servers since April 2016. What’s so special about Pinkslipbot is its capability to use the machine as a control server after it’s being wiped by an antivirus.
What’s so special about QakBot/Pinkslipbot banking trojan?
Also known as QakBot or QBot, Pinkslipbot has been active since 2007. It uses universal plug and play (UPnP) for opening ports to allow incoming connections from anyone on the internet to talk to devices.
This banking malware chiefly targets the US-based enterprises. It looks like a complete threat which has keylogging, password stealing, and man-in-the-middle attack components.
The researchers have also called it the first malware that makes use of infected machines as HTTPS-based control servers.
The infected machines are being used as HTTPS-based proxies to hide the real IP addresses of real control servers. With its army of more than 500,000 infected computers, Pinkslipbot steals more than half-million records every day.
Pinkslipbot’s setup:
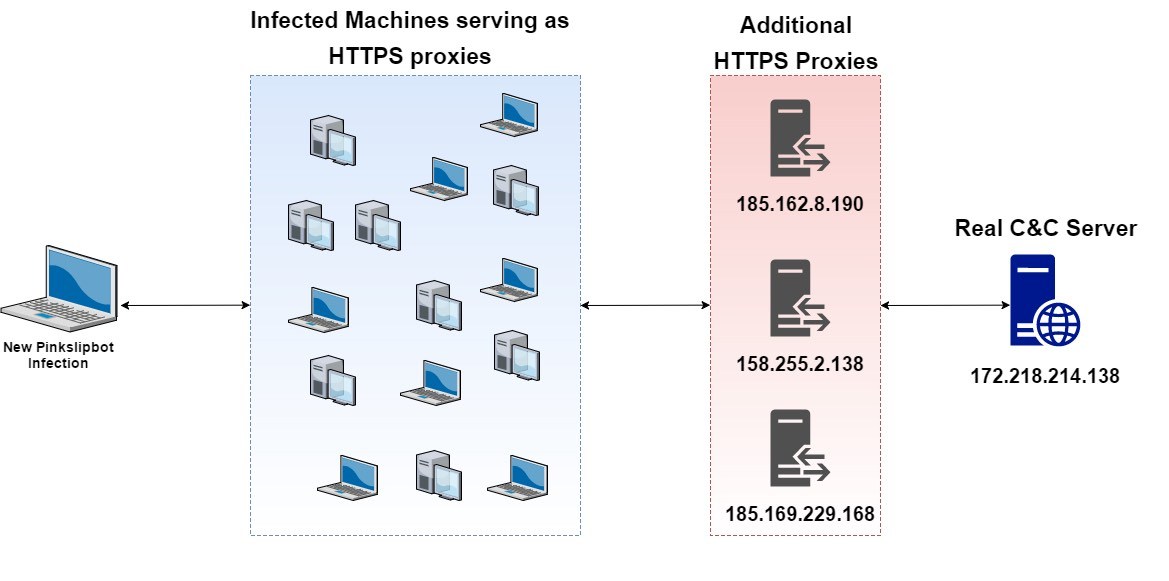
At the moment, the process of turning an infected machine into control server proxy is unknown. The researchers have, however, predicted that this decision is taken if a machine’s IP is located in North America, it has high-speed internet, and it can open an internet gateway device port using UPnP.
After finding a suitable device, its descriptions are scanned for Internet gateway devices (IGD). Then, IGD is checked for connectivity and port-forwarding rules are created by using the AddPortMapping function on the IGD. You can find the all the technical details here on McAfee’s blog.
How to defeat Pinkslipbot?
McAfee has released a free tool that scans PCs for Pinkslipbot proxy server infections and gets rid of notorious port mappings. This utility is needed as the Pinkslipbot’s port forwarding rules are very generic and one can mess up the network configurations.
You can download McAfee’s free Pinkslipbot/QakBot removal tool by using this link. The tool runs in detect mode, and no changes are made to system/router configurations.
Did you find this update on Pinkslipbot malware useful? Like our Facebook page for timely security updates.
Take a look at our most-visited lists of security tools:
Comments
Post a Comment