
Microsoft has released some details on the Fireball malware, which was initially reported by Check Point researchers. Microsoft has pointed out that malware’s magnitude of the threat has been overblown. The company has also listed some precautionary methods to
help the customers ensure their security.arlier this month, the security researchers Check Point Threat Intelligence discovered a high volume threat named Fireball malware, which originated from China. It was found that the malware had infected more than 250 million users worldwide, which mostly included Windows users.
According to the researchers, the malware had two main powers: running malicious code on a machine and manipulating the internet user traffic for earning fraudulent ad revenue. The malware mainly affected India and Brazil. In the latest development, Microsoft has published a blog post about the same and clarified some issues.
Windows Defender Research’s Hamish O’Dea told us that Microsoft’s security teams have been aware of the Fireball malware since 2015. However, according to him, the reported magnitude of the threat might have been overblown.
Throwing some more light on the malware and its behavior, O’Dea says that the Fireball infection is spread chiefly via software bundling, which is a common technique to propagate adware. However, “the Fireball suite often carries clean programs with it. The suite uses these clean programs as host processes to load their malicious code in an attempt to evade behavior-based detection,” he adds.
The most common families in the Fireball suite are:
- BrowserModifier:Win32/SupTab
- BrowserModifier:Win32/Sasquor
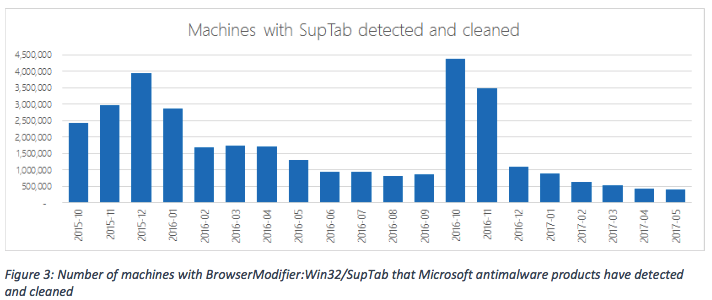
Microsoft points out that Check Point had wrongly estimated the number of infections by basing their results on the number of visits to the search pages. “Not every machine that visits one of these sites is infected with malware. The search pages earn revenue regardless of how a user arrives at the page. Some may be loaded by users who are not infected during normal web browsing, for example, via advertisements or domain parking,” he added.
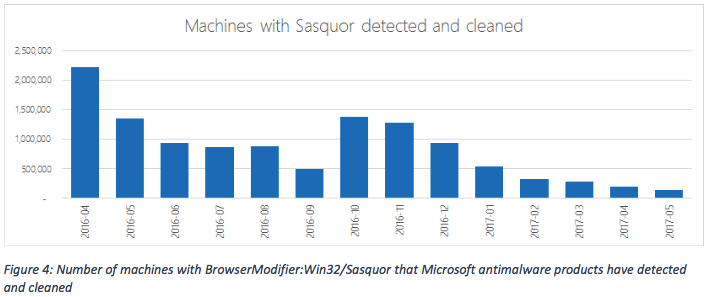
The company also notes that the estimates were made by analyzing the Alexa ranking data, which doesn’t provide a very dependable data. The company has reached out to Check Point and made a request to take another look at their data.
How to protect yourself from Fireball malware?
Microsoft has advised the users to keep their systems and tools like Windows Defender and Microsoft Malicious Software Removal Tools updated.
The users also need to check their Windows Defender exclusion settings to see if the malware made some changes to exclude some folders from the scanning process. For enterprises, the usage of Device Guard has been recommended. One can also request a free evaluation of Windows Defender Advanced Threat Protection.
Comments
Post a Comment