
Brutal Kangaroo malware is the latest addition to the ongoing WikiLeaks Vault 7 leaks. Published earlier this week, the leaked documents show how the CIA hacked offline and air-gapped computers using USB drives. Brutal Kangaroo is basically a combination of 4
tools which work together. The malware used Windows operating system vulnerabilities to targeted air-gapped computers.arlier this month, we told you about the latest leak in the WikiLeaks Vault 7 series. The leaked CherryBlossom firmware was made for taking control of the traffic by finding its way into network routers. Now, WikiLeaks has published the new set of secret documents of which further shed light on CIA’s hacking operations.
The latest documents are 150 pages in length, and they describe a CIA malware toolkit named Brutal Kangaroo for taking control of air-gapped computers by using specialized USB drives. According to WikiLeaks, the components of Brutal Kangaroo create a covert network within the target network, which makes the job easier.
It should be noted that Brutal Kangaroo contains 4 chief components — Drifting Deadline (thumb drive infection tool), Shattered Assurance (server tools for handling thumb drive infection), Broken Promise (postprocessor to take care of the collected information), Shadow (primary persistence mechanism).
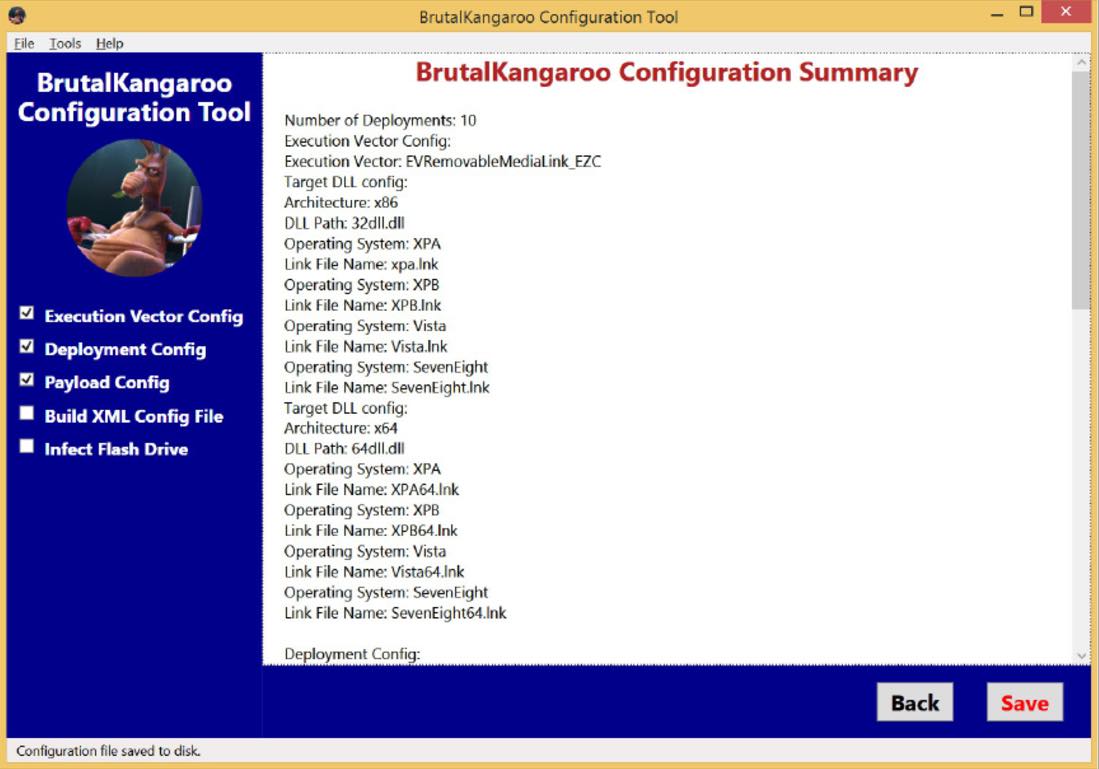
Brutal Kangaroo is able to infect USB thumb drives using a Windows operating system flaw which can be exploited by hand-crafted link files. In the next step, when an infected drive is inserted in the target computer using Windows 7 and .Net 4.5, Drifting Deadline component deploys the malware.
After infection, Shadow scans the other computers connected to the network and infects them. Lastly, Broken Promise scans the data from the air-gapped devices and exfiltrate it.
Brutal Kangaroo malware also supports multiple infections in the same network by using Shadow component. If we combine all the components of Brutal Kangaroo together, it becomes a very useful tool to hack the air-gapped machines.
Comments
Post a Comment