A notorious adware named Judy had managed to break Google Play Store’s security mechanism, affecting about 36.5 million users. Judy malware was spread via 41 popular apps created by a Korean company and tricked users into clicking banner ads to generate illegal revenue. After Check Point reached out to Google, the company removed the apps
from Play Store.ast week, the Check Point researchers uncovered a widespread malware campaign on Google’s official app store. The notorious malware, called Judy, was found on 41 popular apps developed by a fishy Korean company.
The malware is basically an adware that uses tons of fake clicks on the advertisements for generating revenue. As the agent apps became massively popular, the number of affected users might had reached as much as 36.5 million customers.
Some affected apps had existed on Play Store for several years but they were recently updated. The oldest app of the second campaign was updated in April 2016. As per Check Point’s report, it’s unclear how long the rogue code existed in the app.
The security researchers also found many other apps that contained Judy malware. The connection between the two campaigns is unclear. It’s possible that one campaign got the code from other.
How does Judy Malware operate?
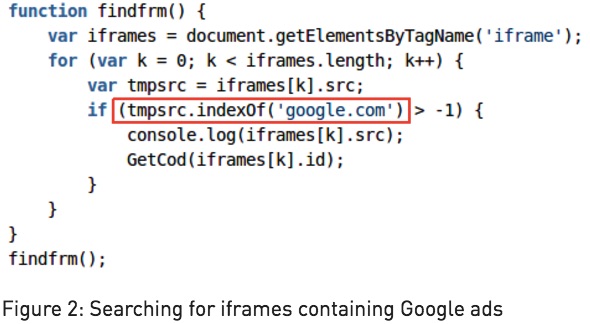
For bypassing Google Play’s protection, Bouncer, the coders of Judy malware created an app that looked innocent. After arriving on a user’s smartphones, the malware established a connection with the C&C server and downloaded the malicious payload, which included JS code, user-agent string, and URLs controlled by malware author.
After this, Judy opened the malicious URL that imitated a PC browser in a hidden web page. It was followed by another redirection that loaded Google Ads and generated illegitimate clicks.
You can find the complete list of Judy malware apps on Check Point blog. If you’re having any of these apps installed on your Android phone, uninstall it and use some security solution to clean your phone.
Did you find this story on Judy malware interesting? Don’t forget to share your feedback with us.

Comments
Post a Comment