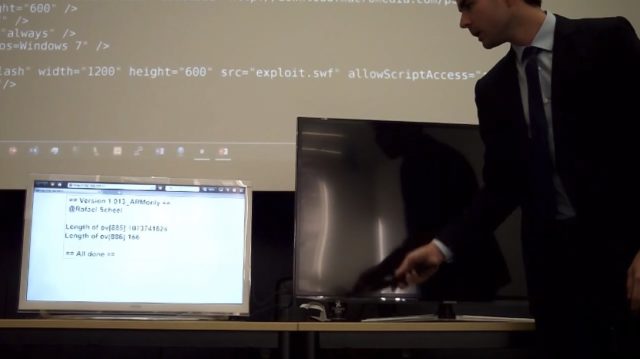
Do you know that your televisions can be easily hacked and used as a spying weapon by an attacker or government. A security researcher recently demonstrated a method that used rogue TV signals, DVB-T to be precise, to gain root access to smart TVs. Moreover, this attack is almost impossible to detect due to the uni-directional nature of TV signals.
hen we wrote about the massive WikiLeaks’ release of CIA’s hacking tools, we told you about a tool called Weeping Angel, which had the potential to control Samsung smart TVs and turn them into spying devices. But, to infect such TVs, CIA needed physical access to install the spyware.
Now, Rafael Scheel, a security researcher working with OneConsult, has developed his own smart TV attack that allows a hacker to use rogue DVB-T (Digital Video Broadcasting-Terrestrial) signals to get root access on the smart TVs. Getting root access means that the attacker would be able to use the device for all kinds of spying and notorious activities.
Scheel’s method was recently presented at a security conference. He showed that the attacker can execute the attack from a remote location without any user interaction. The attack operates in the background, which means that users won’t be able to notice the attack, according to Bleeping computer.
Scheel says that the center of this attack is Hybrid Broadcast Broadband TV (HbbTV). It’s an industry standard that supported by most TV manufacturers and cable providers. Different TV transmission technologies, like DVB-T, support HbbTV.
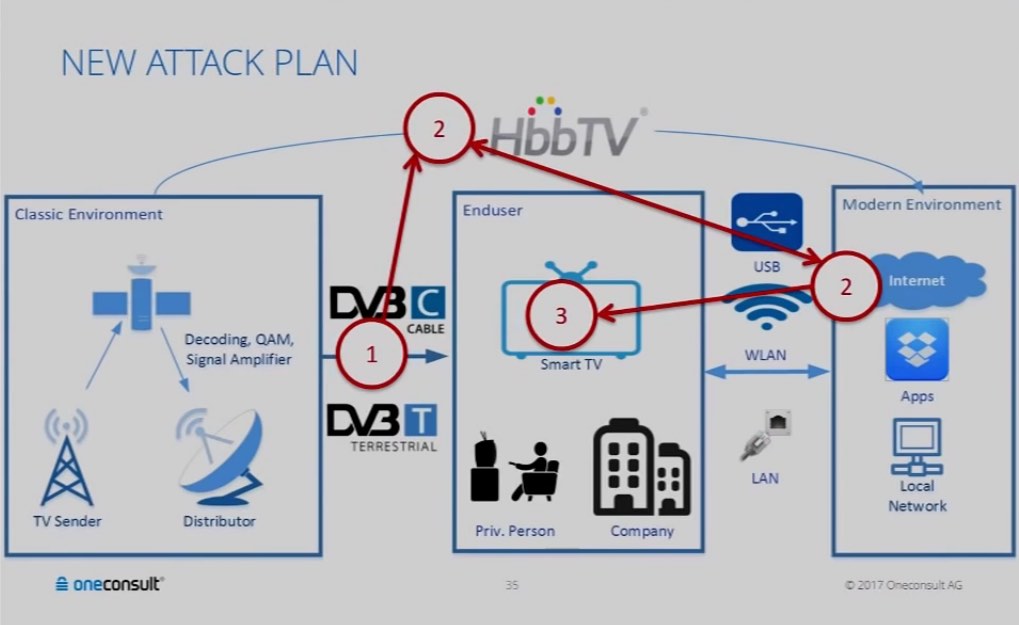
Interestingly, any TV connects to a stronger signal. As the cable providers transmit signals from hundreds of miles away, the rogue DVB-T signals can be transmitted from a nearby house or city. The HbbTV standard helps the attacker send a command that instructs a smart TV to load a malicious website in the background.
Scheel developed two exploits for taking over a device. The first exploit was based on CVE-2015-3090, a zero-day leaked by Hacking Team in 2015. The second exploit helped him gain access to the user’s firmware.
Scheel also says that as DVB-T transmission method for HbbTV commands is uni-directional, which means data flows from attacker to TV only, the discovery of attack is tough. So, the attacker can only be caught transmitting the signals in real-time.
Also, any backdoor created using this technique is almost impossible to remove. In Scheel’s testing, the factory reset operation didn’t help.
You can see the video of the Scheel’s presentation here:
Did you find this remote TV hacking attack interesting? Don’t forget to share your views with us.
Comments
Post a Comment