
Who made the protocol that enables encryption of WhatsApp, Allo, Messenger, and other chat services; What does end-to-end encryption mean; What data exactly do you give away when you use WhatsApp, Messenger, Allo; The most secure alternative of all. Here, we’ll discuss all these apps and the “metadata” collected by them.
verybody knows by now that WhatsApp has enabled end-to-end encryption, for their users. There also have been allegations, speculations, and research about how their end to end encryption has a backdoor that could let third-party people snoop, decrypt and read messages.
Nerd Read Recommendation: WhatsApp Retransmission Vulnerability
But what most of us don’t know, is what information they are already having access to by the pretext of the keyword metadata in their FAQs and public information of details of their information collection phrases.
WhatsApp, Facebook Messenger, Google Allo, and Signal Messaging App uses Signal’s own Protocol by the same name.
Wikipedia says this about Signal Protocol
“The Signal Protocol is a non-federated cryptographic protocol that provides end-to-end encryption for instant messaging conversations. — Wikipedia”
The Signal Protocol was built by Open Whisper System, a nonprofit group that was founded in 2013 by the former Twitter head of security Moxie Marlinspike.
End-to-End encryption provides you the surety that your message is encrypted before sending it to the sender, and that only s/he would decode it using the private key s/he has.
So what’s the problem here, you might ask? Facebook and Google Allo are using the same protocol, it’s secure! Well, Facebook Messenger and Google Allo don’t enable end-to-end encryption by default. Facebook Messenger users have to enable “Secret Conversations” and Google Allo users have to enable Incognito Mode, to leverage encryption.
Alright, Alright, so Facebook and Allo don’t default enable it, but Whatsapp and Signal messaging app so, what’s wrong now? Why not stick with WhatsApp then?
The answers lie in WhatsApp’s collection of metadata.
Metadata has always been a blurry, not so very understood, term simply because it means different things in terms of different applications.
Edward Snowden lights up with what it’s really used for.
In this Electronic Frontier Foundation post by Kurt Opsahl, he gives examples of what companies and governments can get hold of by the somewhat disguised use of the word metadata, getting information on basis of it, such as the following excerpts out of this article:
- They know you rang a phone sex service at 2:24 am and spoke for 18 minutes. But they don’t know what you talked about.
- They know you called a gynecologist, spoke for a half hour, and then called the local Planned Parenthood’s number later that day. But nobody knows what you spoke about.
- They know you spoke with an HIV testing service, then your doctor, then your health insurance company in the same hour. But they don’t know what was discussed.
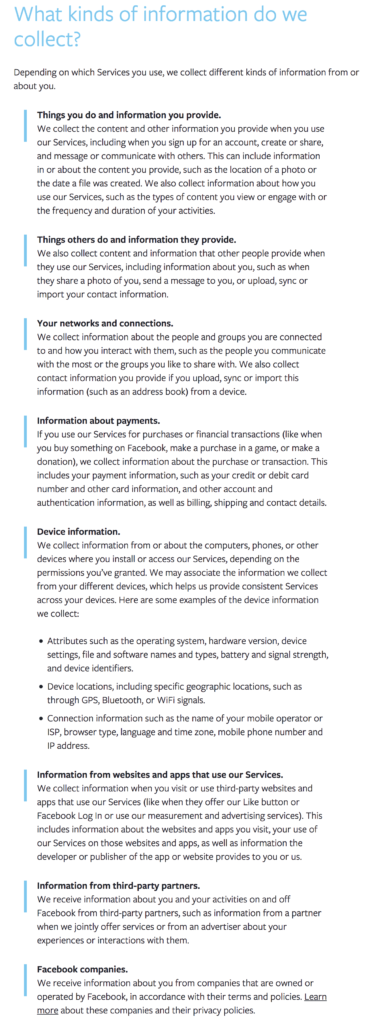
Even though WhatsApp doesn’t store backups on their servers, Whatsapp can collect data when, where, and with whom you communicate, it’s stated rather really vaguely which gives them freedom of sorts, ain’t it? In their own words:
Usage and Log Information. We collect service-related, diagnostic, and performance information. This includes information about your activity (such as how you use our Services, how you interact with others using our Services, and the like), log files, and diagnostic, crash, website, and performance logs and reports.
Besides this, they collect information about your OS, browser information (think your search history on synced devices!), IP address, mobile network data, and phone number. And if they can’t obtain your phone number, they’ll obtain it when people message you, since WhatsApp has access to your friends’ activity data as well.
We won’t talk about Facebook, since everybody knows what we give them when we use their services.
Google Allo has had its fair share of scrutiny.
Signal App retains only the phone number that you register on it with, and the last logged in time on their server, and only the day and no other minute or second.
When you enable WhatsApp’s feature of notifying you about a change in receiver’s key (which is needed for decryption), WhatsApp says it shouldn’t be a concern since receiver’s key can change on the new installation on device or reinstallation of WhatsApp itself, and suggests to continue using it.
Signal has disappearing messages.
“Any conversation can be configured to delete sent and received messages after a specified interval. The configuration applies to all parties of a conversation, and the clock starts ticking for each recipient once they’ve read their copy of the message.”
And the best part? It’s Open Source! Ah!
And it’s free, and it’s advertisement free, and it runs on donations.
Let us know how you found this article! We’re thrilled listening to your feedback.


Comments
Post a Comment